Unifying Cyber Threat Intelligence to Prioritize Vulnerability Remediation & Manage Risk
Accurate and timely cyber threat intelligence is critical to prioritize remediation efforts and protect organizations from intensifying threats. While public vulnerability databases like the National Institute of Standards and Technology’s National Vulnerability Database (NIST NVD) and the Cybersecurity and Infrastructure Security Agency’s Known Exploited Vulnerabilities Catalog (CISA KEV) play a key role, they provide a limited and often lagging view of the threat landscape. Supplementing public domain vulnerability databases with advanced cyber threat intelligence helps overcome these limitations to better assess vulnerabilities and prioritize risk-based remediation efforts.
The Need for Cyber Threat Intelligence
Many teams rely on public domain vulnerability databases to assess vulnerabilities and prioritize remediation. However, these databases often lag behind real-time threats leaving organizations exposed to emerging and sophisticated attacks. The integration of robust cyber threat intelligence solutions helps cover this gap for more effective and risk-based application security posture management.
Cyber threat intelligence solutions augment public vulnerability databases with predictive measures like EPSS, dark web monitoring, social trending, threat actor intelligence, and other data to provide a more accurate and up-to-date threat assessment. Organizations can apply this data to triage and prioritize remediation efforts through manual review processes or by leveraging cyber threat intelligence data to calculate technical risk.
Applying Cyber Threat Intelligence in Practice
Implementing cyber threat intelligence can pose its own set of challenges. Depending on maturity level, organizations may lack advanced sources to leverage for risk assessment and prioritization. Furthermore, connecting threat intelligence data with vulnerabilities to inform prioritization can be cumbersome. Often security engineers must switch contexts between scanning tools where vulnerabilities are detected and threat intelligence feeds with the data needed to assess and triage those vulnerabilities. This creates friction and can inhibit the application of critical data for vulnerability management.
ArmorCode recognizes these challenges and offers flexible solutions to empower organizations of any maturity level to leverage cyber threat intelligence data effectively, consistently, and seamlessly. ArmorCode unifies vulnerability and cyber threat intelligence data in a single platform and leverages this data to assess the technical risk of vulnerabilities and calculate a Risk Score. Instead of security engineers trying to find, manage, and apply threat intelligence data across siloed tools, ArmorCode automatically ingests and applies relevant data to calculate the risk of vulnerabilities and prioritize remediation efforts.
Leveraging Cyber Threat Intelligence to Manage Risk
ArmorCode aggregates cyber threat intelligence data from public domain sources, third-party vendors, internally curated feeds, and native ArmorCode Advanced Threat Intelligence capabilities. Below are three use cases demonstrating how organizations can unify and apply cyber threat intelligence data consistently and seamlessly within ArmorCode.
1. Unifying vulnerabilities and public domain threat intelligence data within ArmorCode
For organizations without a dedicated solution, public domain threat intelligence data provides a good starting point – especially if it is well integrated into the vulnerability assessment and prioritization process. While NIST NVD and CISA KEV may lack the advanced intelligence of specialized solutions, they provide valuable data to assess the technical severity of vulnerabilities. ArmorCode aggregates vulnerabilities and relevant public domain data to provide unified visibility into security posture, calculate risk, and prioritize remediation efforts.
2. Leveraging native ArmorCode Advanced Threat Intelligence to optimize risk-based remediation efforts
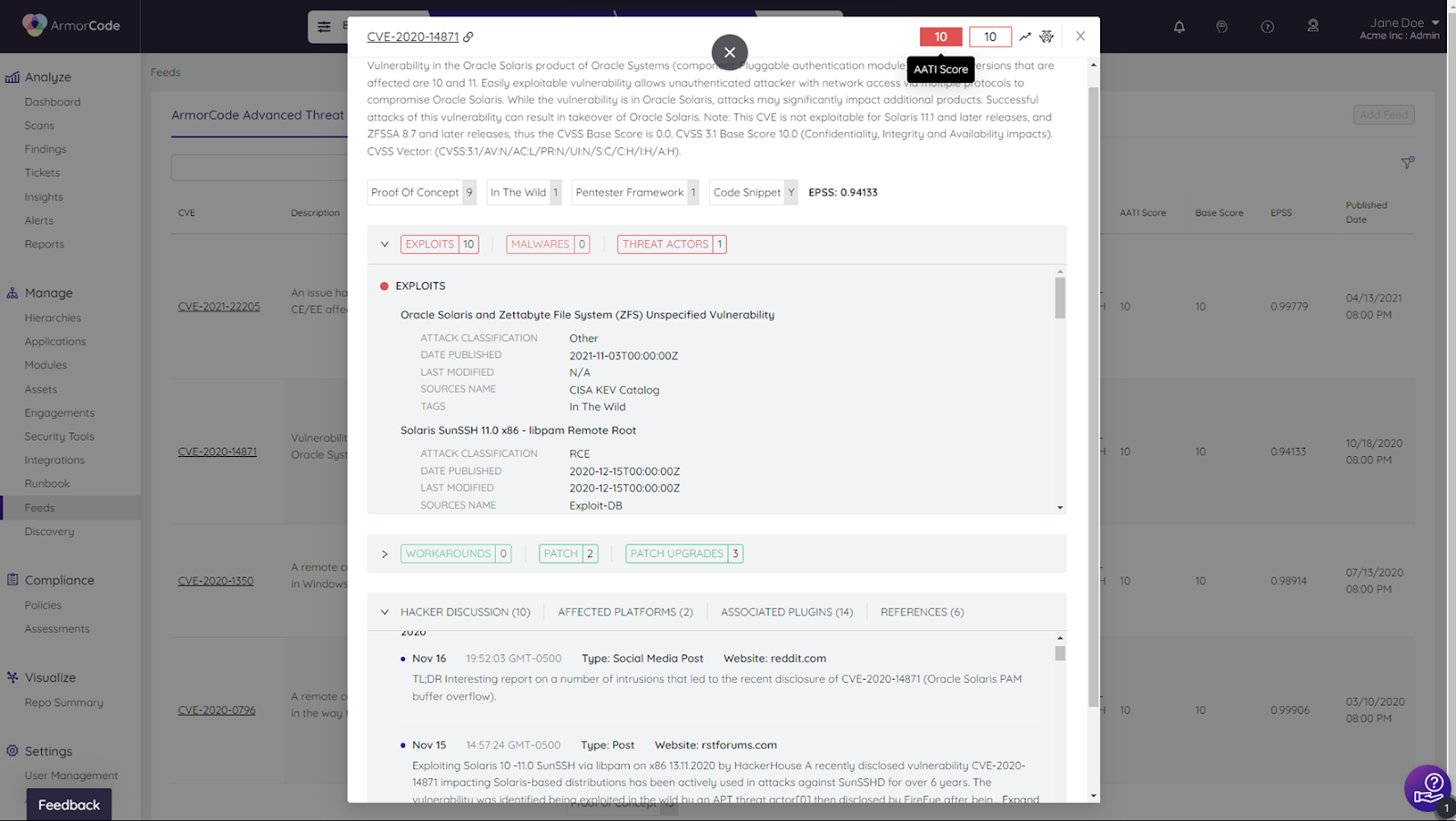
Leveraging advanced threat intelligence data beyond public domain sources helps organizations better assess the immediate and real-world threats of vulnerabilities. For example, ArmorCode Advanced Threat Intelligence (AATI) augments data from public domain sources with EPSS, dark web monitoring, social trending, threat actor intelligence, and other sources to provide a more accurate and timely assessment. ArmorCode leverages this data alongside severity and business context to calculate ArmorCode’s Adaptive Risk Score for vulnerabilities. Organizations can then apply this Risk Score for visibility into their security posture and to automate risk-based triaging and remediation workflows.
3. Integrating internal and third-party cyber threat intelligence feeds within ArmorCode
For organizations with internally curated threat intelligence feeds and/or third-party cyber threat intelligence solutions ArmorCode can ingest data from these sources and make it applicable for vulnerability triaging and ArmorCode Risk Score calculation. This enables organizations to get greater value from investments and leverage key threat intelligence data consistently. To learn more, check out ArmorCode’s integrations or contact us to discuss specific integrations.
The increasing speed and sophistication of cyber attacks necessitate advanced cyber threat intelligence to keep pace. ArmorCode allows organizations to adopt and evolve an approach that aligns with their maturity level, technology stack, and other specific needs. By enabling a consistent, standardized, and unified way to leverage cyber threat intelligence data, organizations can prioritize remediation efforts and manage software risk more efficiently and effectively.
To learn more, schedule a demo or take a self-guided tour of the ArmorCode platform.