The Cyber Insider: This Week in Cyber News

Welcome to The Cyber Insider
—A retrospective on recent cybersecurity news. In this dynamic publication, we bring you the latest and most pressing cybersecurity news and incidents from around the world. In each edition, we unravel the evolving landscape of online threats, data breaches, and cutting-edge solutions to keep you informed and empowered in the digital age. Join us as we navigate the cyber frontier and equip you with the knowledge you need to stay secure in an increasingly connected world.
1. CVSS 4.0 – New Vulnerability Scoring System is Live
FIRST (Forum of Incident Response and Security Teams) has officially announced the highly anticipated release of CVSS v4.0 – the next generation of the Common Vulnerability Scoring System standard. This comes more than eight years after the release of CVSS v3.0 in June 2015 and marks a significant milestone for the cybersecurity industry.
The latest revision of the standard aims to overcome its shortcomings by introducing several new metrics for vulnerability assessment. These metrics include:
- Safety (S)
- Automatable (A)
- Recovery ( R)
- Value Density (V)
- Vulnerability Response Effort (RE)
- Provider Urgency (U)
These supplemental metrics enhance the vulnerability assessment process by providing a more comprehensive analysis of the potential risks and threats
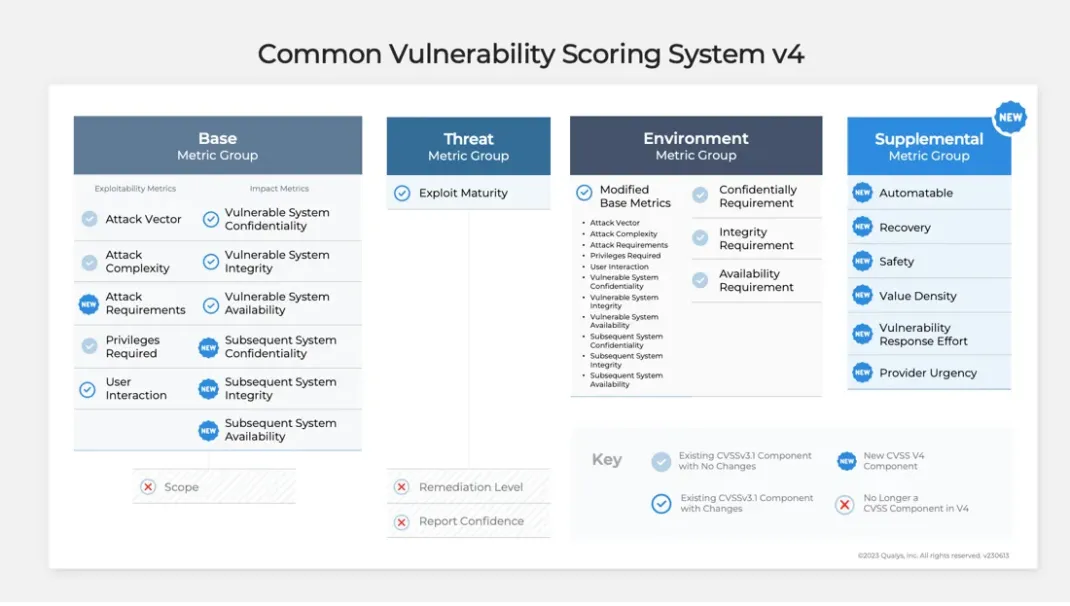
It introduces new nomenclature to enumerate CVSS scores using Base (CVSS-B), Base + Threat (CVSS-BT), Base + Environmental (CVSS-BE), and Base + Threat + Environmental (CVSS-BTE) severity ratings.
References:
CVSS v4.0 User Guide
FIRST Announces CVSS 4.0 – New Vulnerability Scoring System
CVSS v4 Is Now Live and What You Need To Know About It
2. Data Exposure Misconfiguration Issue in ServiceNow
In mid-October, a researcher named Aaron Costello pointed out a misconfiguration in the ServiceNow widget called “Simple List” that caused potential data exposure. The misconfiguration was related to the issue in the Access Control List (ACL) that allowed unauthenticated users to access data remotely.
ACLs encompass a three-part validation process involving “roles, conditions, and scripts.“
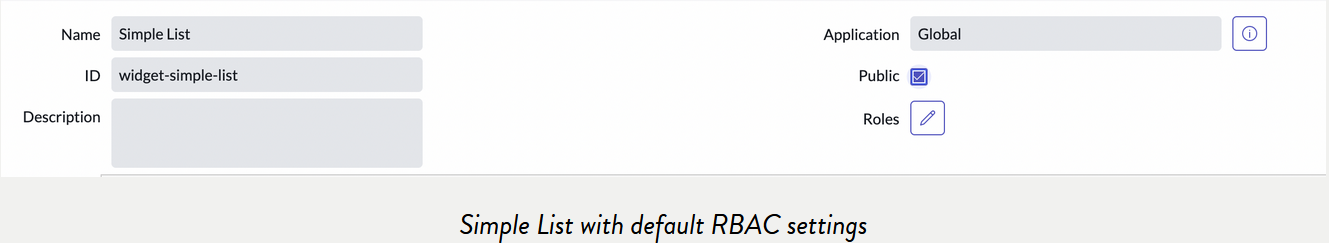
In the above image, it can be observed that the widget is allowed “public access” but no role has been defined for the same, which is a default behavior.
In cases where an Access Control List (ACL) is not explicitly defined for a particular resource, the standard response is to prohibit access. Nevertheless, when a resource is linked to an ACL with all three validation components left unconfigured, access attempts are authorized, potentially introducing a security vulnerability.
Aaron Costello’s research showed that many ServiceNow ACLs are left blank, leaving them vulnerable to potential attackers.
Remediation
- Please ensure that the Access Control Lists (ACLs) are configured and present in your instance.
- Consider amending the ACL by incorporating the script line “gs.isLoggedIn()” into its script section.
- Evaluate public widgets and consider deactivating them if not aligned with use cases.
- Inspect Access Control Lists (ACLs) that are either empty or contain the “Public” role.
- Consider implementing stricter access controls like IP Address Access Control or Adaptive Authentication within ServiceNow.
References:
ServiceNow Data Exposure: A Wake-Up Call for Companies
ServiceNow quietly fixes 8-year-old data exposure flaw
Data Exposure and ServiceNow: The Elephant in the ITSM Room — Enumerated (Report by Aaron Costello)
3. “CVE-2023-22518 – Improper Authorization Vulnerability In Confluence Data Center and Server”
Class: Improper Authorization
CWE: CWE-285 / CWE-266
ATT&CK: T1548.002
On 31st October, Atlassian warned of a severe vulnerability in Confluence. “CVE-2023-22518 – Improper Authorization Vulnerability In Confluence Data Center and Server”, (the on-prem versions of Atlassian’s products) affects all the versions of Confluence, and Atlassian classified it as as critical (9.1 with the following vector CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:H) per their internal assessment.
No active exploits of the vulnerability have been reported. Atlassian confirmed that confidentiality is not affected as attackers cannot exfiltrate any instance data.
No additional information about the vulnerability or the specific method that could be used to exploit it has been disclosed. This is likely because doing so could aid malicious actors in creating an attack.
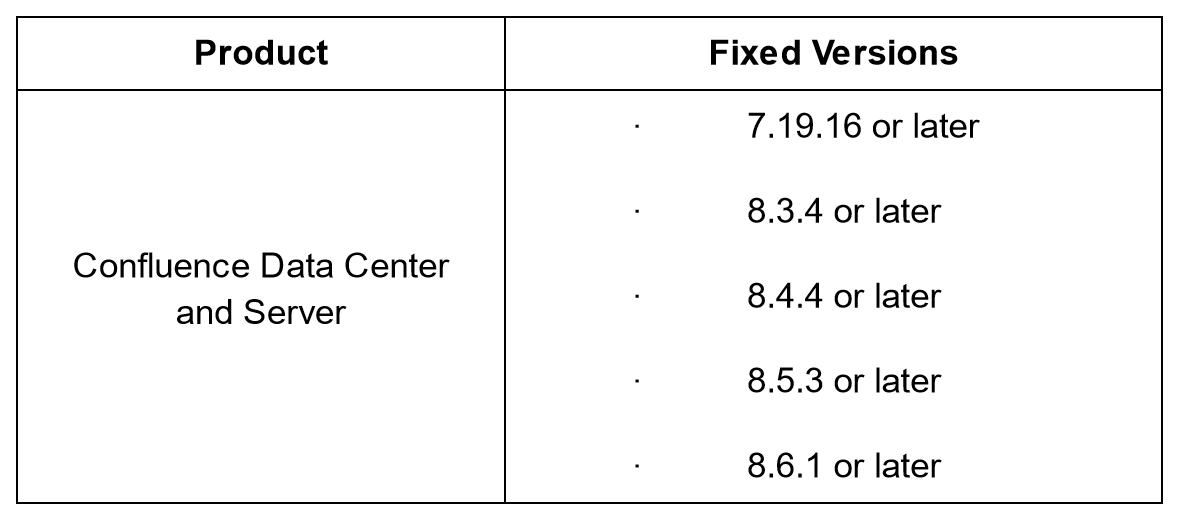
Remediation
Atlassian recommends that you patch each of your affected installations to one of the listed fixed versions (or any later version) below.
Apply temporary mitigations if unable to patch
- Back up your instance
- Remove your instance from the internet until you can patch it, if possible.