1. Actively Exploited Zero-Day Vulnerability in Chrome
Google has proactively addressed a critical security concern with the release of a pivotal update for Chrome. This update encompasses seven crucial security fixes, one of which has already been exploited.
The identified zero-day vulnerability is assigned CVE-2023-6345 and is deemed a high-severity issue. This classification stems from an integer overflow bug present in Skia, an open-source 2D graphics library.
According to the National Institute of Standards and Technology’s (NIST) National Vulnerability Database (NVD), the vulnerability impacts Chrome versions preceding 119.0.6045.199. It enables a remote attacker, who has compromised the renderer process, to potentially execute a sandbox escape through a malicious file.
The most recent Chrome update marks the resolution of a total of seven zero-day vulnerabilities addressed throughout the year.
- CVE-2023-2033 (CVSS score: 8.8) – Type confusion in V8
- CVE-2023-2136 (CVSS score: 9.6) – Integer overflow in Skia
- CVE-2023-3079 (CVSS score: 8.8) – Type confusion in V8
- CVE-2023-4762 (CVSS score: 8.8) – Type confusion in V8
- CVE-2023-4863 (CVSS score: 8.8) – Heap buffer overflow in WebP
- CVE-2023-5217 (CVSS score: 8.8) – Heap buffer overflow in vp8 encoding in libvpx
Users are recommended to upgrade to Chrome version 119.0.6045.199/.200 for Windows and 119.0.6045.199 for macOS and Linux to mitigate potential threats.
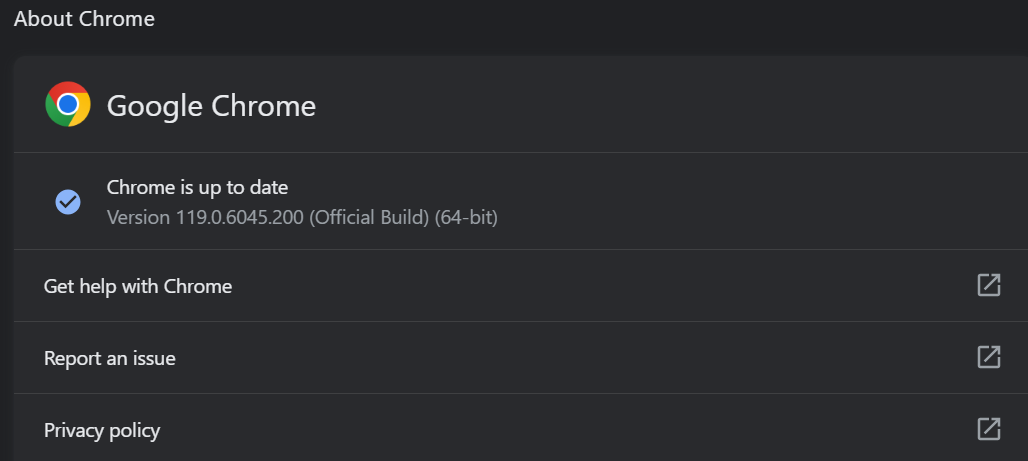
Credit for the discovery and reporting of the flaw on November 24, 2023, goes to Benoît Sevens and Clément Lecigne from Google’s Threat Analysis Group (TAG).
References
Stable Channel Update for Desktop
Zero-Day Alert: Google Chrome Under Active Attack, Exploiting New Vulnerability
Google Patches Another Chrome Zero-Day as Browser Attacks Mount
2. Apple Unveils Two Newly Discovered Zero-Day Exploits Targeting iPhones and Macs
“Apple is aware of a report that this issue may have been exploited against versions of iOS before iOS 16.7.1,” the company said in an advisory issued on Wednesday.
In response to ongoing cyber threats, Apple has urgently released security updates to rectify two zero-day vulnerabilities that were actively exploited in attacks affecting iPhone, iPad, and Mac devices.
The identified vulnerabilities are associated with the WebKit browser engine and are designated as CVE-2023-42916 and CVE-2023-42917.
Exploiting these bugs, attackers could potentially access sensitive information through an out-of-bounds read weakness and execute arbitrary code via a memory corruption bug. These vulnerabilities are leveraged by maliciously crafted webpages.
Apple has addressed these security concerns in devices running iOS 17.1.2, iPadOS 17.1.2, macOS Sonoma 14.1.2, and Safari 17.1.2.
The remediation involves enhanced input validation and tightening security measures to mitigate the risks posed by these vulnerabilities. The list of impacted Apple devices is quite extensive, and it includes:
- iPhone XS and later
- iPad Pro 12.9-inch 2nd generation and later, iPad Pro 10.5-inch, iPad Pro 11-inch 1st generation and later, iPad Air 3rd generation and later, iPad 6th generation and later, and iPad mini 5th generation and later
- Macs running macOS Monterey, Ventura, Sonoma
Clément Lecigne of Google’s Threat Analysis Group (TAG) has been credited with discovering and reporting the twin flaws.
With the latest security fixes, Apple has remediated as many as 19 actively exploited zero-days since the start of 2023.
References
Zero-Day Alert: Apple Rolls Out iOS, macOS, and Safari Patches for 2 Actively Exploited Flaws
macOS Sonoma 14.1.2 Update (23B92) & (23B2091) Safari Zero Day!
3. Microsoft urgently warns of three zero-day vulnerabilities, urging swift action for enhanced cybersecurity
CVE-2023-36025: Windows SmartScreen Bypass
Description: Vulnerability allowing malicious content to bypass Windows SmartScreen security feature.
Attack Vector: Exploited through booby-trapped links in shortcut files.
Kevin Breen’s Insight: Emails with .url attachments or logs with processes spawning from .url files are high-priority for threat hunters.
CVE-2023-36033: DWM Core Library Vulnerability
Description: Exploitable vulnerability in the “DWM Core Library” in Microsoft Windows.
Exploitation: Actively exploited in the wild as a zero-day and publicly disclosed before patches were available.
Impact: Affects Windows 10 and later, as well as Windows Server 2019 and subsequent versions.
Mike Walters’ Insight: Local exploitation with low complexity, no high-level privileges, or user interaction required. Attackers could gain SYSTEM privileges, making it an efficient method for privilege escalation, particularly after initial access through methods like phishing.
CVE-2023-36036: Windows Cloud Files Mini Filter Driver
Description: Vulnerability affecting the “Windows Cloud Files Mini Filter Driver.”
Impact: Affects Windows 10 and later, as well as Windows Server 2008 and later.
Exploitation: Microsoft notes it’s relatively straightforward for attackers to exploit CVE-2023-36036 to elevate their privileges on a compromised PC.
Stay vigilant and prioritize necessary actions to address these critical vulnerabilities and enhance your overall security posture.
References
Microsoft Patch Tuesday, November 2023 Edition
Microsoft and Adobe Patch Tuesday, November 2023 Security Update Review
Microsoft Patch Tuesday – November 2023
4. Secrets exposed in app images on Docker Hub
The Docker Hub store has revealed a concerning security lapse, with at least 5,493 container images found to harbor secrets, potentially exposing sensitive information. This alarming discovery accounts for 54% of the 10,178 Docker Hub images subjected to analysis.
These compromised containers, which contained confidential data, were downloaded an astonishing 132 billion times by users on the widely utilized Docker Hub platform.
In their investigation, Cybernews researchers meticulously scrutinized and extracted a staggering 191,529 secrets from 5,493 publicly shared container images. Eliminating duplicates reduced the count to 48,481 unique secrets.
The exposed secrets encompassed a wide range of sensitive information, including API or SSH keys, access control tokens, internal use URLs, and even private credentials. Notably, these divulged secrets exhibited a correlation with the most commonly employed web services among developers.
GitHub tokens emerged as the most frequently neglected secrets, constituting 26.6% of the total secrets identified, totaling 51,038 instances.
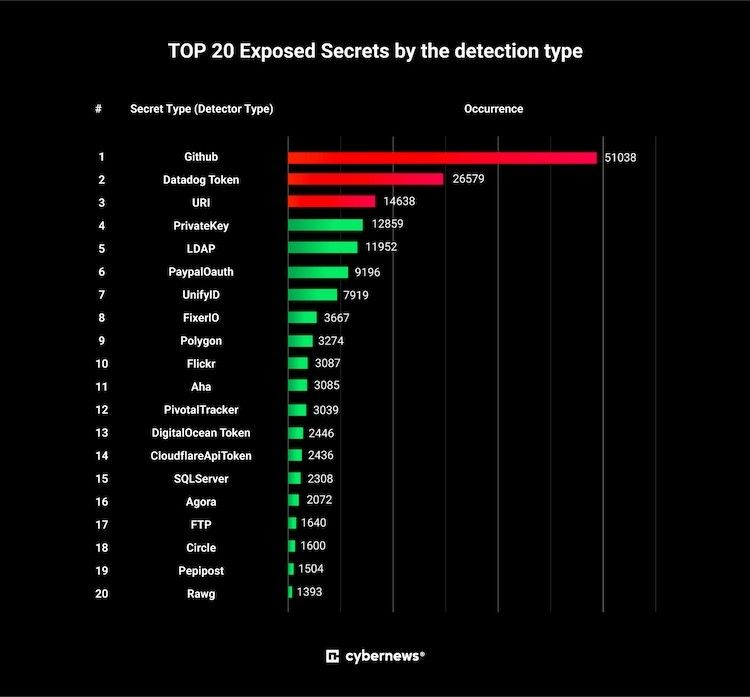
The second most neglected secret (13.9%) is Datadog Tokens, risking unauthorized access and manipulation on the Datadog monitoring platform.
Uniform Resource Identifiers (7.6%) expose potential unauthorized access and data manipulation. Less common but highly dangerous secrets include 9,196 PayPal OAuth and 7,919 UnifyID secrets, posing risks to financial and identity-related data.
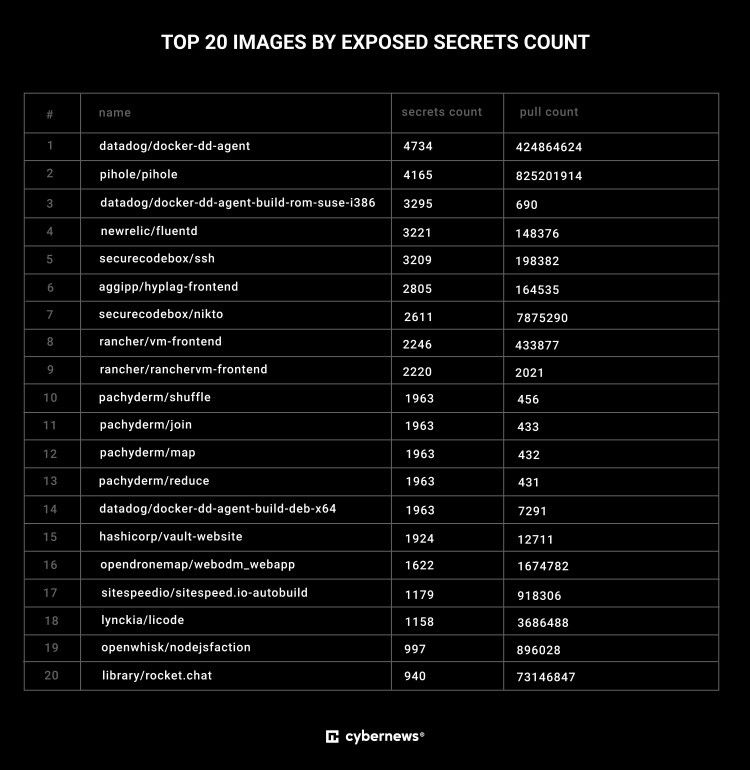
Additionally, thousands of scraped secrets encompass DigitalOcean, Cloudflare API, SQLServer, FTP, and other sensitive credentials and tokens.
References
Thousands of secrets lurk in app images on Docker Hub
Thousands of secrets lurk in app images on Docker Hub | Cybernews