The Cyber Insider: Week 12/11 – 12/17

1. Atlassian Issues Critical Software Fixes to Prevent RCE
Atlassian has issued security advisories for four critical remote code execution vulnerabilities that affect Confluence, Jira, and Bitbucket servers, in addition to a companion macOS application.
The following are the four vulnerabilities:
- CVE-2023-22522: A critical template injection flaw has been identified, enabling authenticated users, including those with anonymous access, to introduce insecure input into Confluence pages. This vulnerability carries a severity score of 9.0 and affects all Confluence Data Center and Server versions from 4.0.0 to 8.5.3.
- CVE-2023-22523: A critical Privileged Remote Code Execution (RCE) issue has been discovered in the Assets Discovery agent, impacting Jira Service Management Cloud, Server, and Data Center with a severity score of 9.8. Vulnerable versions of Asset Discovery include those below 3.2.0 for Cloud and 6.2.0 for Data Center and Server.
- CVE-2023-22524: A critical security flaw involves the bypass of blocklist and macOS Gatekeeper on the companion app for Confluence Server and Data Center for macOS. This vulnerability affects all versions of the app prior to 2.0.0 and carries a severity score of 9.6.
- CVE-2022-1471: A critical Remote Code Execution (RCE) vulnerability has been identified in the SnakeYAML library, impacting multiple versions of Jira, Bitbucket, and Confluence products. This security issue carries a severity score of 9.8.
Mitigation
To address all four of the above problems, users are recommended to update to one of the following product versions:
- Confluence Data Center and Server 7.19.17 (LTS), 8.4.5, and 8.5.4 (LTS)
- Jira Service Management Cloud (Assets Discovery) 3.2.0 or later, and Jira Service Management Data Center and Server (Assets Discovery) 6.2.0 or later.
- Atlassian Companion App for MacOS 2.0.0 or later
- Automation for Jira (A4J) Marketplace App 9.0.2, and 8.2.4
- Bitbucket Data Center and Server 7.21.16 (LTS), 8.8.7, 8.9.4 (LTS), 8.10.4, 8.11.3, 8.12.1, 8.13.0, 8.14.0, 8.15.0 (Data Center Only), and 8.16.0 (Data Center Only)
- Confluence Cloud Migration App (CCMA) 3.4.0
- Jira Core Data Center and Server, Jira Software Data Center and Server 9.11.2, 9.12.0 (LTS), and 9.4.14 (LTS)
- Jira Service Management Data Center and Server 5.11.2, 5.12.0 (LTS), and 5.4.14 (LTS)
References
Atlassian patches critical RCE flaws across multiple products
CVE-2023-22522 – RCE Vulnerability In Confluence Data Center and Confluence Server
Atlassian Releases Critical Software Fixes to Prevent Remote Code Execution
CVE-2023-22523 – RCE Vulnerability in Assets Discovery
CVE-2023-22524 – RCE Vulnerability in Atlassian Companion App for MacOS
CVE-2022-1471 – SnakeYAML library RCE Vulnerability impacts Multiple Products
2. Microsoft’s Final 2023 Patch Tuesday: 4 Critical Fixes, 33 Vulnerabilities Addressed
Microsoft’s latest Patch Tuesday updates for December 2023 marked the final release of the year, addressing a total of 33 vulnerabilities across its software. This release stands out as one of the lighter ones in recent memory.
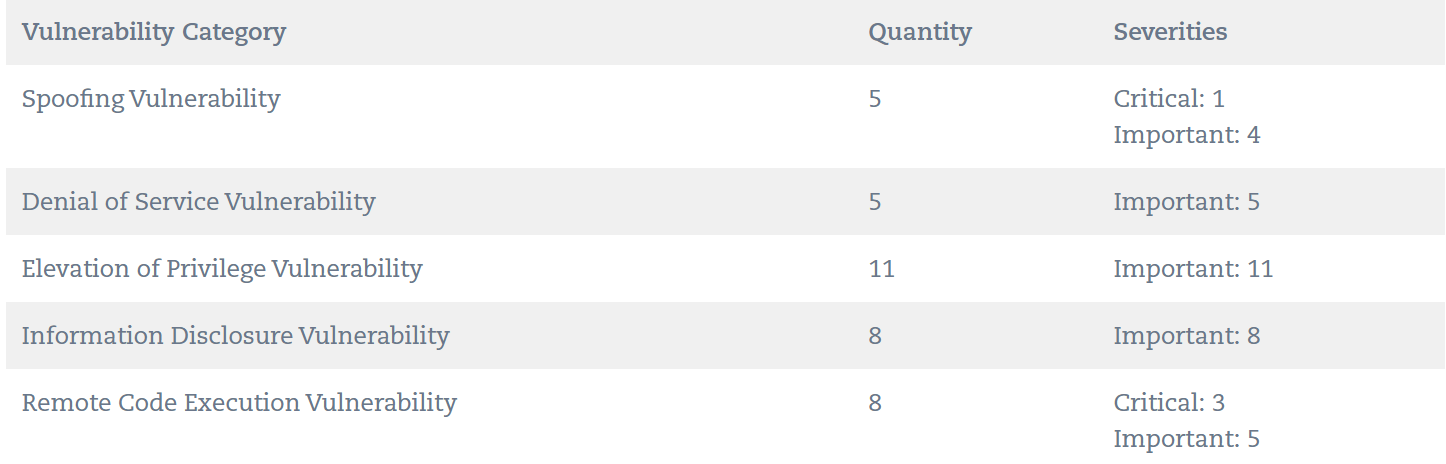
Among the identified flaws, four are classified as Critical, while the remaining 29 are rated as Important in terms of severity.
Complementing these updates, Microsoft has also resolved 18 vulnerabilities in its Chromium-based Edge browser since the November 2023 Patch Tuesday release.
Some important CVEs from the latest patch:
- CVE-2023-36019 (CVSS score: 9.6) – Microsoft Power Platform Connector Spoofing Vulnerability
- CVE-2023-35630 (CVSS score: 8.8) – Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
- CVE-2023-35639 (CVSS score: 8.8) – Microsoft ODBC Driver Remote Code Execution Vulnerability
- CVE-2023-35641 (CVSS score: 8.8) – Internet Connection Sharing (ICS) Remote Code Execution Vulnerability
- CVE-2023-35628 (CVSS score: 8.1) – Windows MSHTML Platform Remote Code Execution Vulnerability
- CVE-2023-35638 (CVSS score: 7.5) – DHCP Server Service Denial-of-Service Vulnerability
- CVE-2023-35643 (CVSS score: 7.5) – DHCP Server Service Information Disclosure Vulnerability
- CVE-2023-35642 (CVSS score: 6.5) – Internet Connection Sharing (ICS) Denial-of-Service Vulnerability
- CVE-2023-35636 (CVSS score: 6.5) – Microsoft Outlook Information Disclosure Vulnerability
- CVE-2023-36012 (CVSS score: 5.3) – DHCP Server Service Information Disclosure Vulnerability
The comprehensive December edition covers a range of software components, including Microsoft Office and Components, Windows Win32K, Windows Kernel, Microsoft Bluetooth Driver, Windows DHCP Server, Windows ODBC Driver, and more.
The fixes encompass various security concerns such as Denial of Service (DoS), Elevation of Privilege (EoP), Information Disclosure, Remote Code Execution (RCE), and Spoofing. Microsoft’s proactive approach ensures a strengthened security posture for users across diverse software platforms.
Microsoft has patched more than 900 flaws this year, making it one of the busiest years for software patching according to the Zero Day Initiative’s data.
References
Microsoft December 2023 Security Updates
Microsoft and Adobe Patch Tuesday, December 2023 Security Update Review
Microsoft’s Final 2023 Patch Tuesday: 33 Flaws Fixed, Including 4 Critical
3. Apple Rolls Out Crucial Updates to Address Critical Flaws in iOS and macOS
Apple released security updates for iOS, iPadOS, macOS, tvOS, watchOS, and Safari. These patches address multiple vulnerabilities, including two zero-days for older devices.
In iOS and iPadOS, 12 vulnerabilities were fixed, spanning various components. macOS Sonoma 14.2 resolves 39 issues, including six affecting the ncurses library.
Notable is CVE-2023-45866, a critical Bluetooth flaw allowing keystroke injection in privileged network positions.
Safari 17.2 addresses WebKit flaws (CVE-2023-42890 and CVE-2023-42883) causing arbitrary code execution and a denial-of-service. This update applies to Macs running macOS Monterey and macOS Ventura.
iOS 17.2 and iPadOS 17.2 introduce Contact Key Verification, fixing a Siri bug and enhancing iMessage privacy.
Apple also released iOS 16.7.3 and iPadOS 16.7.3, addressing eight security issues, including two actively exploited WebKit vulnerabilities. These have been patched in tvOS 17.2 and watchOS 10.2. No details on the exploitation nature or threat actors are available yet.
References
Apache Patches Critical RCE Vulnerability in Struts 2
New Critical RCE Vulnerability Discovered in Apache Struts 2 – Patch Now
4. Critical Remote Code Execution Vulnerability Uncovered in Apache Struts 2
Apache has issued a security advisory alerting users to a critical vulnerability in the Struts 2 open-source web application framework, posing a significant risk of remote code execution. Identified as CVE-2023-50164, the flaw originates from a flawed “file upload logic,” potentially allowing unauthorized path traversal.
Struts 2, a Java framework utilizing the Model-View-Controller (MVC) architecture, is employed for constructing enterprise-centric web applications. The discovery and disclosure of this vulnerability credit Steven Seeley of Source Incite.
The impacted software versions include
- Struts 2.3.37 (End of Life)
- Struts 2.5.0 to Struts 2.5.32
- Struts 6.0.0 to Struts 6.3.0
Patches addressing the vulnerability are accessible in versions 2.5.33 and 6.3.0.2 or later, with no alternative workarounds available.
Although there is currently no evidence of the vulnerability being actively exploited in real-world attacks, it is worth noting that a previous security flaw in Struts (CVE-2017-5638, CVSS score: 10.0) was exploited by threat actors in 2017 to compromise the security of consumer credit reporting agency Equifax.
Mitigation
- Update your Struts 2 to version 2.5.33 and 6.3.0.2 or later.
References
New Critical RCE Vulnerability Discovered in Apache Struts 2 – Update Now
New Critical RCE Vulnerability Discovered in Apache Struts 2 – Patch Now
Apache Patches Critical RCE Vulnerability in Struts 2
5. Warning: Adversaries Exploiting AWS STS for Unauthorized Access to Cloud Accounts
AWS Security Token Service (STS) is a web service designed to facilitate the issuance of short-term access tokens to AWS users, including federated users authenticated through third-party identity platforms.
- STS tokens have a fixed duration, not exceeding 36 hours. Once this timeframe elapses, the access and permissions granted by the token are automatically revoked.
- STS tokens are user-specific, ensuring that users do not possess credentials susceptible to easy theft.
Malicious actors can steal long-term Identity and Access Management (IAM) tokens through diverse methods, such as malware infections, publicly exposed credentials, and phishing emails. Subsequently, they exploit these stolen tokens to ascertain the roles and privileges associated with them through API calls.
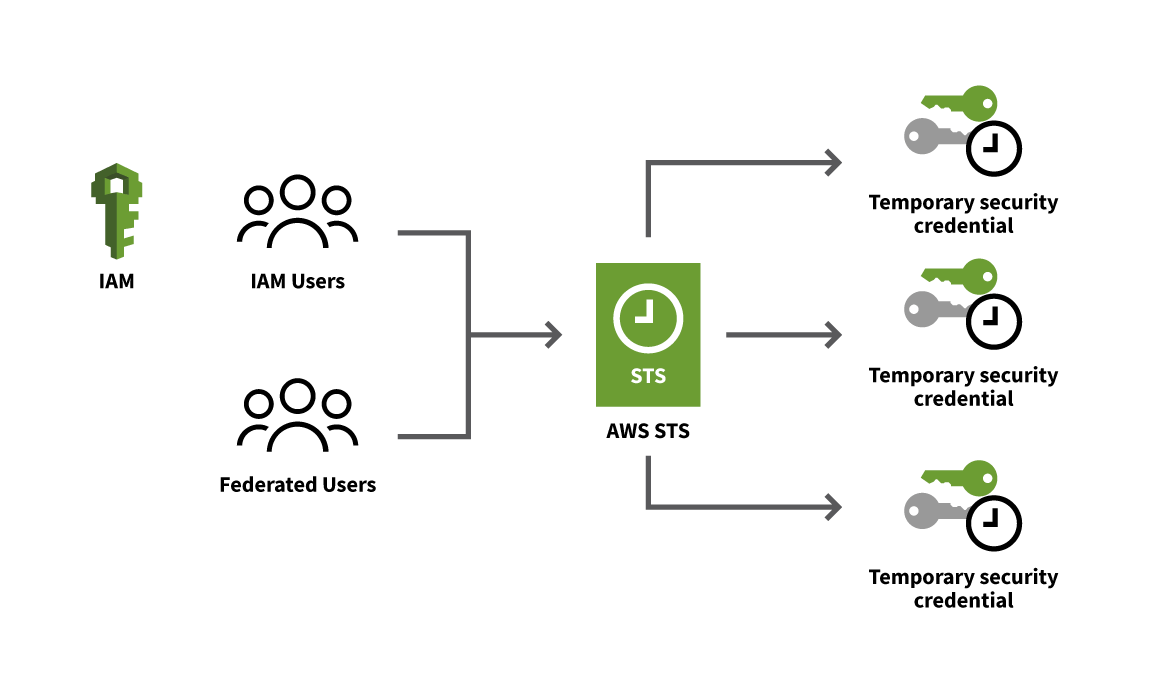
Process of generating STS
“Depending on the token’s permission level, adversaries may also be able to use it to create additional IAM users with long-term AKIA tokens to ensure persistence if their initial AKIA token and all of the ASIA short-term tokens it generated are discovered and revoked,” the researcher said.
In the subsequent phase, a Multi-Factor Authentication (MFA)-authenticated Security Token Service (STS) token generates multiple new short-term tokens. This is followed by the execution of post-exploitation actions, including but not limited to data exfiltration.
If the compromised IAM token or credential is valid, an adversary can then execute API calls or perform actions like aws:MultiFactorAuthPresent, aws:MultiFactorAuthAge, and extract MFA code and device details.
Responding to identified compromise
- Revoke permissions for all temporary credentials that have been verified to be exploited in the attack.
- Delete or rotate long-term Identity and Access Management (IAM) user access keys (AKIA tokens) associated with the compromise.
- Attach a specific “Deny-All” IAM policy to the IAM users (AKIA tokens) engaged in suspicious activity.
- Remove any resources created by the adversary during the unauthorized access.
To prevent AWS token abuse, it is recommended to log CloudTrail events, detect role-chaining and MFA abuse, and rotate long-term IAM user access keys.
References
AWS STS Threat Allows Cloud Infiltration
By the same token: How adversaries infiltrate AWS cloud accounts
Alert: Threat Actors Can Leverage AWS STS to Infiltrate Cloud Accounts