1. Terrapin Vulnerability (CVE-2023-48795) Exposes SSH Protocol to Security Downgrade
Researchers at Ruhr University Bochum have identified a critical vulnerability named Terrapin (CVE-2023-48795, CVSS score: 5.9) in the SSH cryptographic protocol.
This marks the “first ever practically exploitable prefix truncation attack,” allowing attackers to compromise an SSH connection’s integrity and security downgrade.
Terrapin exploits a flaw during SSH extension negotiation, enabling an active adversary-in-the-middle to manipulate connection traffic at the TCP/IP layer.
By truncating the extension negotiation message (RFC8308), the attacker can force the use of less secure client authentication algorithms and deactivate specific countermeasures in OpenSSH 9.5.
Successful attacks hinge on exploiting a vulnerable encryption mode, such as ChaCha20-Poly1305 or CBC with Encrypt-then-MAC.
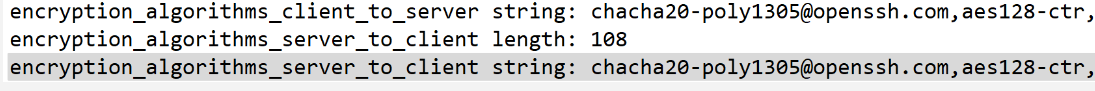
The vulnerability affects various SSH client and server implementations, including OpenSSH, Paramiko, PuTTY, KiTTY, WinSCP, libssh, libssh2, AsyncSSH, FileZilla, and Dropbear. Maintainers have released patches to address the issue.
Mitigation
Organizations, especially those with extensive, interconnected networks, are urged to promptly apply these patches to mitigate the risks associated with the Terrapin vulnerability.
- Disable the vulnerable ChaCha20-Poly1305 cipher in the OpenSSH client and server configurations.
- Disable the aes(128|192|256)-cbc and any EtM MACs when connecting using Paramiko.
References
https://thehackernews.com/2024/01/new-terrapin-flaw-could-let-attackers.html
https://nvd.nist.gov/vuln/detail/CVE-2023-48795
https://jfrog.com/blog/ssh-protocol-flaw-terrapin-attack-cve-2023-48795-all-you-need-to-know/
2. Microsoft’s January 2024 Patch: 2 Critical Fixes out of 48
In the January 2024 Patch Tuesday updates, Microsoft has addressed a total of 48 security vulnerabilities across its software. Among these, two are classified as Critical, while the remaining 46 are rated as Important in severity.
In addition to the aforementioned fixes, nine security vulnerabilities in the Chromium-based Edge browser including addressing a zero-day vulnerability (CVE-2023-7024, CVSS score: 8.8) that Google reported as actively exploited in the wild.
The most critical vulnerabilities addressed in the January updates are:
- CVE-2024-20674 (CVSS score: 9.0) – Windows Kerberos Security Feature Bypass Vulnerability: This flaw allows authentication feature bypass, enabling impersonation. Successful exploitation requires an authenticated attacker to conduct a machine-in-the-middle (MitM) attack or other local network spoofing techniques, sending a malicious Kerberos message to the victim machine.
- CVE-2024-20700 (CVSS score: 7.5) – Windows Hyper-V Remote Code Execution Vulnerability: Authentication is not required for exploitation, and it does not necessitate user interaction. However, a race condition must be won to stage a remote code execution attack.
Notable flaws also include CVE-2024-20653 (CVSS score: 7.8), a privilege escalation flaw affecting the Common Log File System (CLFS) driver, and CVE-2024-0056 (CVSS score: 8.7), a security bypass impacting System.Data.SqlClient and Microsoft.Data.SqlClient.
Furthermore, Microsoft highlighted the disablement of the ability to insert FBX files in Word, Excel, PowerPoint, and Outlook in Windows by default due to a security flaw (CVE-2024-20677, CVSS score: 7.8) that could lead to remote code execution.
References
https://thehackernews.com/2024/01/microsofts-january-2024-windows-update.html
https://msrc.microsoft.com/update-guide/releaseNote/2024-Jan
https://www.thurrott.com/windows/295905/microsoft-releases-january-2024-patch-tuesday-updates
3. CISA Flags 6 Critical Security Vulnerabilities
The Cybersecurity and Infrastructure Security Agency (CISA) has identified and added six security vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, all of which show evidence of ongoing exploitation.
One highlighted CVE-2023-27524 (CVSS score: 8.9), is a high-severity flaw in Apache Superset, enabling remote code execution. It was fixed in version 2.1 after being reported in April 2023 by Horizon3.ai’s Naveen Sunkavally, who identified it as a “dangerous default configuration” allowing unauthorized access for code execution, credential harvesting, and data compromise.
Additionally, CISA included five other flaws in its KEV catalog:
- CVE-2023-38203 (CVSS score: 9.8) – Adobe ColdFusion Deserialization of Untrusted Data Vulnerability
- CVE-2023-29300 (CVSS score: 9.8) – Adobe ColdFusion Deserialization of Untrusted Data Vulnerability
- CVE-2023-41990 (CVSS score: 7.8) – Apple Multiple Products Code Execution Vulnerability
- CVE-2016-20017 (CVSS score: 9.8) – D-Link DSL-2750B Devices Command Injection Vulnerability
- CVE-2023-23752 (CVSS score: 5.3) – Joomla! Improper Access Control Vulnerability. Affects Joomla! CMS versions 4.0.0-4.2.7
Mitigation
To mitigate the risks posed by these vulnerabilities, the Federal Civilian Executive Branch (FCEB) agencies are advised to apply the necessary fixes by January 29, 2024, to enhance the security of their networks against active threats.
- Upgrade Joomla to version 4.2.8 or the latest.
- Update your Apple devices to tvOS 16.3, iOS 16.3 and iPadOS 16.3, macOS Monterey 12.6.8, macOS Big Sur 11.7.9, iOS 15.7.8 and iPadOS 15.7.8, macOS Ventura 13.2, and watchOS 9.3.
- Update your Apache Superset to the newest version and change the default value for SECRET_KEY config.
- Adobe recommends updating your ColdFusion JDK/JRE LTS version to the latest update release.
References
https://thehackernews.com/2024/01/cisa-flags-6-vulnerabilities-apple.html
https://www.cisa.gov/news-events/alerts/2024/01/08/cisa-adds-six-known-exploited-vulnerabilities-catalog
https://www.cisa.gov/known-exploited-vulnerabilities-catalog
4. Critical Chrome Zero-Day Vulnerability Exploited – Immediate Update Required
Google has issued urgent security updates for Chrome to address an actively exploited zero-day vulnerability tracked as CVE-2023-7024.
Discovered by Clément Lecigne and Vlad Stolyarov, the identified vulnerability is characterized as a heap-based buffer overflow flaw within the WebRTC framework. This vulnerability poses a significant risk, potentially leading to program crashes or the execution of arbitrary code.
Given that WebRTC is an open-source project and that it’s also supported by Mozilla Firefox and Apple Safari, it’s currently not clear if the flaw has any impact beyond Chrome and Chromium-based browsers.
The development marks the resolution of the eighth actively exploited zero-day in Chrome since the start of the year.
- CVE-2023-2033 (CVSS score: 8.8) – Type confusion in V8
- CVE-2023-2136 (CVSS score: 9.6) – Integer overflow in Skia
- CVE-2023-3079 (CVSS score: 8.8) – Type confusion in V8
- CVE-2023-4762 (CVSS score: 8.8) – Type confusion in V8
- CVE-2023-4863 (CVSS score: 8.8) – Heap buffer overflow in WebP
- CVE-2023-5217 (CVSS score: 8.8) – Heap buffer overflow in vp8 encoding in libvpx
- CVE-2023-6345 (CVSS score: 9.6) – Integer overflow in Skia
Mitigation
- Users are strongly advised to update to Chrome version 120.0.6099.129/130 for Windows and 120.0.6099.129 for macOS and Linux to mitigate potential threats.
- Chromium-based browser users (Microsoft Edge, Brave, Opera, Vivaldi) should also apply fixes promptly upon release to ensure security.
References
https://thehackernews.com/2023/12/urgent-new-chrome-zero-day.html
https://www.darkreading.com/cloud-security/google-eighth-zero-day-patch-2023-chrome
https://www.bleepingcomputer.com/news/security/google-fixes-8th-chrome-zero-day-exploited-in-attacks-this-year/
5. CVE-2024-20272: Critical Cisco Unity Connection Flaw
A high-severity vulnerability (CVE-2024-20272) within Cisco Unity Connection’s web management interface poses a significant security risk. This flaw, an unauthenticated arbitrary file upload, could allow attackers to execute commands on the underlying system, compromise data, and even gain root privileges.
Discovered by security researcher Maxim Suslov, the vulnerability stems from a lack of authentication in a specific API and inadequate validation of user-supplied data. Exploiting this weakness, an attacker could upload malicious files, potentially granting them complete control over the affected system.
Cisco released software updates promptly to address this critical issue. Affected versions include:
- Unity Connection 12.5 and earlier
- Unity Connection 14
While Cisco swiftly provided fixes for this and additional medium-severity vulnerabilities in other products, including Identity Services Engine and ThousandEyes Enterprise Agent, unfortunately, a fix for the command injection bug in WAP371 (CVE-2024-20287) will not be provided as this device reached end-of-life in June 2019.
Mitigation
- Unity Connection 12.5 and earlier: Upgrade to version 12.5.1.19017-4 or later.
- Unity Connection 14: Upgrade to version 14.0.1.14006-5 or later.
- Migrate to the Cisco Business 240AC Access Point as the WAP371 has reached end-of-life and will not receive a fix.
References
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-cuc-unauth-afu-FROYsCsD
https://thehackernews.com/2024/01/cisco-fixes-high-risk-vulnerability.html
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-sb-wap-inject-bHStWgXO