The Cyber Insider: Week 1/22 – 1/28

1. Multiple Vulnerabilities in GitLab: Urgent Update Required
GitLab released versions 16.7.2, 16.6.4, and 16.5.6 for GitLab Community Edition (CE) and Enterprise Edition (EE) that contain important security fixes.
Title Severity
Account Takeover via password reset Critical
without user interactions
Bypass CODEOWNERS approval removal High
An attacker can abuse Slack/Mattermost High
integrations to execute slash commands
as another user
Workspaces able to be created under Medium
different root namespace
Commit signature validation ignores Low
headers after the signature
- CVE-2023-7028(Account Takeover via password reset without user interactions): A vulnerability has been identified in GitLab CE/EE across multiple versions: 16.1 to 16.1.6, 16.2 to 16.2.9, 16.3 to 16.3.7, 16.4 to 16.4.5, 16.5 to 16.5.6, 16.6 to 16.6.4, and 16.7 to 16.7.2. This issue pertains to the inadvertent delivery of user account password reset emails to unverified email addresses. It is classified as a Critical severity problem with a CVSS score of 10.0
- CVE-2023-4812(Bypass CODEOWNERS approval removal): An issue has been identified in GitLab, affecting versions from 15.3 before 16.5.5, 16.6 before 16.6.4, and 16.7 before 16.7.2. The vulnerability allows bypassing required CODEOWNERS approval by adding changes to a previously approved merge request. This is categorized as a high-severity issue.
- CVE-2023-5356 (An attacker can abuse Slack/Mattermost integrations to execute slash commands as another user): Incorrect authorization checks in GitLab CE/EE, spanning versions from 8.13 before 16.5.6, 16.6 before 16.6.4, and 16.7 before 16.7.2, enable a user to abuse Slack/Mattermost integrations to execute slash commands as another user. This is identified as a high-severity issue.
- CVE-2023-6955 (Workspaces able to be created under different root namespace): An improper access control vulnerability exists in GitLab Remote Development, impacting all versions prior to 16.5.6, 16.6 prior to 16.6.4, and 16.7 prior to 16.7.2. This vulnerability allows an attacker to create a workspace in one group associated with an agent from another group. It is classified as a medium-severity issue.
- CVE-2023-2030 (Commit signature validation ignores headers after the signature): An issue has been discovered in GitLab CE/EE, affecting versions from 12.2 prior to 16.5.6, 16.6 prior to 16.6.4, and 16.7 prior to 16.7.2. This vulnerability allows an attacker to modify the metadata of signed commits potentially, and it is categorized as a low-severity issue.
Mitigation
- Upgrade to these versions 16.7.2, 16.6.4, 16.5.6 immediately.
- Enable Two-Factor Authentication (2FA) for all GitLab accounts
- Rotate all secrets stored in GitLab
References
https://about.gitlab.com/releases/2024/01/11/critical-security-release-gitlab-16-7-2-released/
https://www.cvedetails.com/vulnerability-list/vendor_id-13074/Gitlab.html
2. Zero-Day Alert in Chrome: Urgent Update Required
The identified issue denoted as CVE-2024-0519, revolves around an out-of-bounds memory access in the V8 JavaScript and WebAssembly engine, posing a potential crash trigger that malicious actors could exploit.
The National Vulnerability Database (NVD) from NIST describes the flaw as “Out-of-bounds memory access in V8 in Google Chrome prior to 120.0.6099.224,” highlighting that a remote attacker could potentially exploit heap corruption through a crafted HTML page.
According to MITRE’s Common Weakness Enumeration (CWE), exploiting out-of-bounds memory access enables attackers to read secret values, including memory addresses. This information could then be used to bypass protection mechanisms like ASLR, potentially enhancing the reliability and likelihood of exploiting other vulnerabilities for code execution rather than just causing denial of service.
Specific details about the attacks and the threat actors involved have been intentionally withheld to prevent further exploitation. The issue was reported anonymously on January 11, 2024.
Mitigation
- Users are strongly advised to upgrade to Chrome version 120.0.6099.224/225 for Windows, 120.0.6099.234 for macOS, and 120.0.6099.224 for Linux.
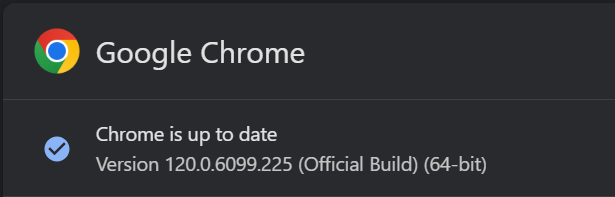
- Additionally, users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are encouraged to promptly apply any available fixes to protect their browsers against potential exploitation.
References
https://thehackernews.com/2024/01/zero-day-alert-update-chrome-now-to-fix.html
https://nvd.nist.gov/vuln/detail/CVE-2024-0519-
https://cwe.mitre.org/data/definitions/125.html
3. GitHub Addresses High-Severity Vulnerabilities: CVE-2024-0200 and CVE-2024-0507
GitHub has rotated certain keys following the discovery of a high-severity vulnerability that could potentially allow unauthorized access to credentials in a production container.
As a precautionary measure, GitHub rotated exposed credentials, including the commit signing key, GitHub Actions, GitHub Codespaces, and Dependabot customer encryption keys.
The identified vulnerability tracked as CVE-2024-0200 (CVSS score: 7.2), has no evidence of prior exploitation in the wild. It also affects the GitHub Enterprise Server (GHES), but successful exploitation requires an authenticated user with an organization owner role logged into a GHES instance, mitigating potential risks.
GitHub described the vulnerability as an “unsafe reflection” issue in GHES, leading to reflection injection and remote code execution. The patch has been implemented in GHES versions 3.8.13, 3.9.8, 3.10.5, and 3.11.3.
Additionally, GitHub addressed another high-severity bug, tracked as CVE-2024-0507 (CVSS score: 6.5), allowing an attacker with access to a Management Console user account with the editor role to escalate privileges via command injection.
Mitigation
- Update to GHES versions 3.8.13, 3.9.8, 3.10.5, and 3.11.3.
- Users relying on above mentioned keys are advised to import the updated versions.
References
https://github.blog/2024-01-16-rotating-credentials-for-github-com-and-new-ghes-patches/
https://thehackernews.com/2024/01/github-rotates-keys-after-high-severity.html
https://docs.github.com/en/enterprise-server@3.11/admin/release-notes
https://nvd.nist.gov/vuln/detail/CVE-2024-0200
https://nvd.nist.gov/vuln/detail/CVE-2024-0507
4. CVE-2023-34063: VMware Addresses Aria Automation Vulnerability
VMware has disclosed a critical security vulnerability, CVE-2023-34063 (CVSS score: 9.9), in Aria Automation (formerly vRealize Automation).
This flaw, characterized as a “missing access control” issue, could allow an authenticated attacker to gain unauthorized access to remote organizations and workflows.
The discovery credit goes to the Commonwealth Scientific and Industrial Research Organization’s (CSIRO) Scientific Computing Platforms team.
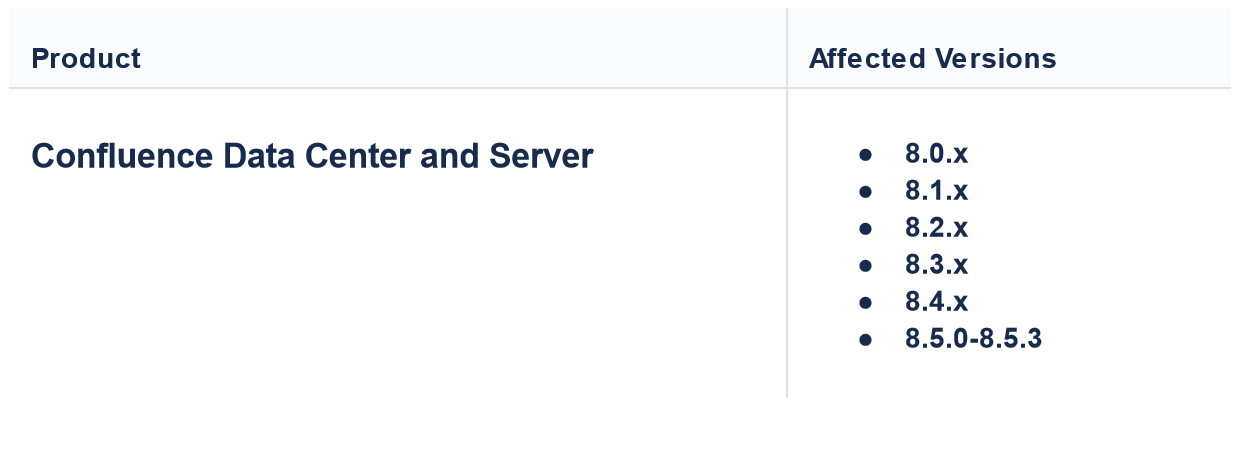
Impacted versions include VMware Aria Automation (8.11.x, 8.12.x, 8.13.x, and 8.14.x) and VMware Cloud Foundation (4.x and 5.x).
Mitigation
- Apply the provided patch and upgrade to version 8.16
References
https://core.vmware.com/resource/vmsa-2024-0001-questions-answers
https://www.vmware.com/security/advisories/VMSA-2024-0001.html
5. Critical CVE-2023-22527: Remote Code Execution Vulnerability in Confluence
Atlassian has disclosed a critical remote code execution (RCE) vulnerability, identified as CVE-2023-22527, with a maximum CVSS score of 10.0.
Atlassian Cloud Instances are not affected by CVE-2023-22527. If your Confluence site is accessed via an atlassian.net domain, it is hosted by Atlassian and is not exposed to this vulnerability.
In case anonymous access is disabled on your public instance, the vulnerability remains an unauthenticated remote code execution threat, making it exploitable even in the absence of anonymous access.
The vulnerability arises from a template injection issue on outdated versions of Confluence Data Center and Server, enabling an unauthenticated attacker to achieve RCE on affected versions.
Atlassian has released patches in versions 8.5.4, 8.5.5 (Confluence Data Center and Server), 8.6.0, 8.7.1, and 8.7.2 (Data Center only). This development coincides with Atlassian’s release of patches for more than two dozen vulnerabilities, underscoring the importance of timely updates for security measures.
Mitigation
- Update Confluence Data Center and Server to 8.5.4 or 8.5.5
- Update Confluence Data Center to 8.6.0, 8.7.1, or 8.7.2
References
https://confluence.atlassian.com/kb/faq-for-cve-2023-22527-1332810917.html
https://confluence.atlassian.com/security/cve-2023-22527-rce-remote-code-execution-vulnerability-in-confluence-data-center-and-confluence-server-1333990257.html