On September 8, 2025, the JavaScript ecosystem experienced one of its most significant supply chain attacks—the NPM supply chain attack— when attackers compromised multiple maintainer accounts through a sophisticated phishing campaign. What initially appeared to be 18 compromised packages has expanded as security researchers continue to discover additional affected libraries, with at least 27 packages now confirmed to be compromised, affecting billions of weekly downloads across the JavaScript ecosystem.
The Attack Vector: Social Engineering at Scale
The attack began with a meticulously planned phishing campaign targeting NPM package maintainers. Josh Junon, maintainer of critical JavaScript infrastructure packages, provided insight into the attack vector on Hacker News:
“Email came from support at npmjs dot help. Looked legitimate at first glance. Not making excuses, just had a long week and a panicky morning and was just trying to knock something off my list of to-dos. Made the mistake of clicking the link instead of going directly to the site like I normally would (since I was mobile).“
The attackers had registered the domain npmjs.help on September 5, 2025, creating a convincing impersonation of NPM’s legitimate infrastructure. The phishing emails claimed urgent 2FA updates were required by September 10, 2025, exploiting maintainer fatigue and creating artificial urgency.
Timeline of the NPM Supply Chain Attack (UTC)
September 4, 2025
- Attackers register the malicious domain “npmjs.help”
September 8, 2025
- Phishing emails sent to multiple NPM maintainers
- First malicious packages published to the NPM registry
- Automated security systems detect anomalous code patterns
- Josh Junon publicly acknowledges compromise
- Community identifies discrepancies in package repositories
- NPM begins removing malicious packages
- Initial wave of malicious versions unpublished from the registry
September 9-11, 2025
- Ongoing discovery of additional compromised packages
- CVE assignments begin for affected packages
- Maintainers regain control and publish fixes or revert to safe versions
Technical Analysis: Sophisticated Malware Implementation
The injected malware demonstrated advanced obfuscation techniques using hexadecimal encoding and complex function structures. The code operated exclusively in browser environments, targeting cryptocurrency transactions through several mechanisms:
- API Hooking: Intercepted window.ethereum, fetch, and XMLHttpRequest calls
- Address Replacement: Used Levenshtein distance algorithms to find similar-looking addresses
- Multi-chain Support: Targeted Ethereum, Bitcoin, Solana, Tron, Litecoin, and Bitcoin Cash
- Persistence: Maintained over 280 hardcoded attacker addresses for redundancy
The malware’s browser-only execution meant server-side Node.js applications were not directly affected, though the potential for future attacks targeting server environments remains a critical concern.
Immediate Actions for Organizations
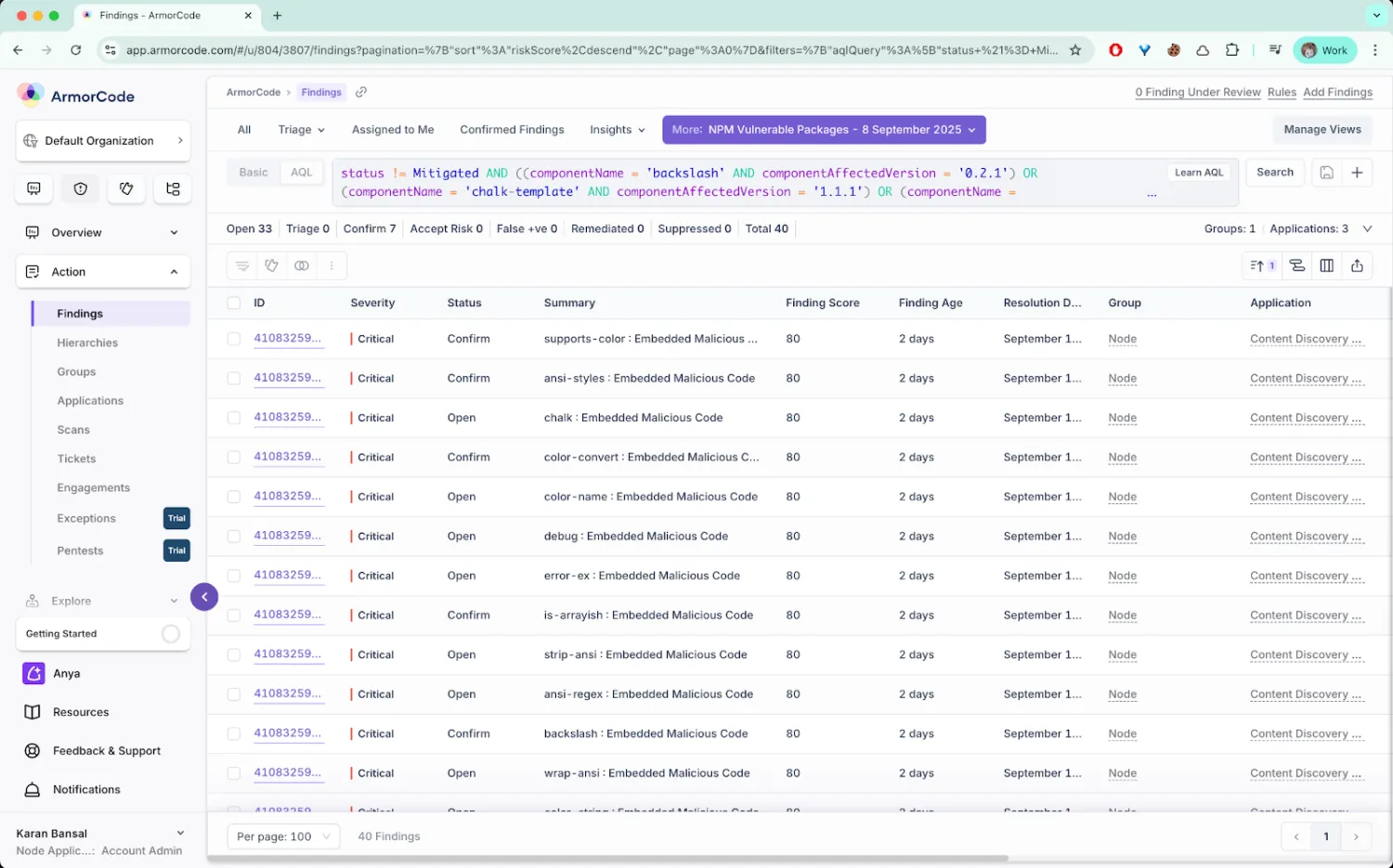
1. Identify Outstanding Issues using the ArmorCode ASPM Platform
Go to the view “NPM Vulnerable Packages – 8 September 2025“ on the ArmorCode Findings page to identify all the unresolved findings in your system.
2. Update or Revert All Affected Packages
Critical: Some packages require downgrades to safe versions, while others have published fixes:
# Packages requiring UPGRADE to new fixed versions (15 packages)
npm install chalk@5.6.2 chalk-template@1.1.2 supports-hyperlinks@4.1.2 \
has-ansi@6.0.2 slice-ansi@7.1.2 wrap-ansi@9.0.2 ansi-regex@6.2.2 \
supports-color@10.2.2 strip-ansi@7.1.2 ansi-styles@6.2.3 \
duckdb@1.3.4 @duckdb/node-api@1.3.4-alpha.27 \
@duckdb/node-bindings@1.3.4-alpha.27 @duckdb/duckdb-wasm@1.30.0 \
prebid.js@10.10.0
# Packages requiring REVERT to previous safe versions (12 packages)
npm install backslash@0.2.0 simple-swizzle@0.2.2 color-string@2.1.0 \
error-ex@1.3.2 color-name@2.0.0 is-arrayish@0.3.2 color-convert@3.1.0 \
debug@4.4.1 proto-tinker-wc@0.1.86 @coveops/abi@2.0.0 \
prebid-universal-creative@1.17.2
# Clear all caches to ensure a clean installation
npm cache clean –force
3. Verify Package Integrity
Check package signatures and compare against known good hashes:
npm pack [package-name]
shasum -a 256 [package-name]-[version].tgz
4. Implement Strict Dependency Pinning
Lock all dependencies to exact versions in package.json:
“dependencies”: {
“ansi-regex”: “6.2.2”,
“ansi-styles”: “6.2.3”,
“backslash”: “0.2.0”,
“chalk”: “5.6.2”,
“chalk-template”: “1.1.2”,
“color-convert”: “3.1.0”,
“color-name”: “2.0.0”,
“color-string”: “2.1.0”,
“debug”: “4.4.1”,
“error-ex”: “1.3.2”,
“has-ansi”: “6.0.2”,
“is-arrayish”: “0.3.2”,
“simple-swizzle”: “0.2.2”,
“slice-ansi”: “7.1.2”,
“strip-ansi”: “7.1.2”,
“supports-color”: “10.2.2”,
“supports-hyperlinks”: “4.1.2”,
“wrap-ansi”: “9.0.2”,
“proto-tinker-wc”: “0.1.86”,
“duckdb”: “1.3.4”,
“@duckdb/node-api”: “1.3.4-alpha.27”,
“@duckdb/node-bindings”: “1.3.4-alpha.27”,
“@duckdb/duckdb-wasm”: “1.30.0”,
“@coveops/abi”: “2.0.0”,
“prebid.js”: “10.10.0”,
“prebid-universal-creative”: “1.17.2”
}
Long-term Security Enhancements
Supply Chain Governance Framework: Establish formal policies requiring security review periods before any dependency updates reach production. Implement staged rollouts with canary deployments for package updates.
Comprehensive SBOM Management: Maintain real-time Software Bill of Materials for all applications, enabling rapid identification of affected systems during supply chain incidents.
Automated Security Monitoring: Deploy continuous monitoring solutions that detect behavioral changes in dependencies, unusual network requests, or unexpected code modifications.
Developer Security Training: Institute mandatory security awareness training focusing on social engineering tactics, with emphasis on verifying sender authenticity and recognizing urgency-based manipulation.
Zero Trust Architecture: Implement runtime application self-protection (RASP) and assume all external dependencies are potentially compromised.
Complete List of Compromised NPM Packages*
| Package | Vulnerable Version | Fix Version | Action | CVE |
| backslash | 0.2.1 | 0.2.0 | Revert | – |
| chalk-template | 1.1.1 | 1.1.2 | Upgrade | – |
| supports-hyperlinks | 4.1.1 | 4.1.2 | Upgrade | – |
| has-ansi | 6.0.1 | 6.0.2 | Upgrade | – |
| simple-swizzle | 0.2.3 | 0.2.2 | Revert | – |
| color-string | 2.1.1 | 2.1.0 | Revert | – |
| error-ex | 1.3.3 | 1.3.2 | Revert | – |
| color-name | 2.0.1 | 2.0.0 | Revert | – |
| is-arrayish | 0.3.3 | 0.3.2 | Revert | – |
| slice-ansi | 7.1.1 | 7.1.2 | Upgrade | – |
| color-convert | 3.1.1 | 3.1.0 | Revert | – |
| wrap-ansi | 9.0.1 | 9.0.2 | Upgrade | – |
| ansi-regex | 6.2.1 | 6.2.2 | Upgrade | – |
| supports-color | 10.2.1 | 10.2.2 | Upgrade | – |
| strip-ansi | 7.1.1 | 7.1.2 | Upgrade | – |
| chalk | 5.6.1 | 5.6.2 | Upgrade | – |
| debug | 4.4.2 | 4.4.1 | Revert | – |
| ansi-styles | 6.2.2 | 6.2.3 | Upgrade | – |
| proto-tinker-wc | 0.1.87 | 0.1.86 | Revert | – |
| duckdb | 1.3.3 | 1.3.4 | Upgrade | CVE-2025-59037 |
| @duckdb/node-api | 1.3.3 | 1.3.4-alpha.27 | Upgrade | CVE-2025-59037 |
| @duckdb/node-bindings | 1.3.3 | 1.3.4-alpha.27 | Upgrade | CVE-2025-59037 |
| @duckdb/duckdb-wasm | 1.29.2 | 1.30.0 | Upgrade | CVE-2025-59037 |
| @coveops/abi | 2.0.1 | 2.0.0 | Revert | – |
| prebid.js | 10.9.1 | 10.10.0 | Upgrade | CVE-2025-59038 |
| prebid.js | 10.9.2 | 10.10.0 | Upgrade | – |
| prebid-universal-creative | 1.17.3 | 1.17.2 | Revert | CVE-2025-59039 |
Note: Some packages require reverting to previous versions (downgrade) as maintainers removed malicious versions without publishing new fixes. Others have published new patched versions (upgrade). Verify the correct action for each package in your dependency tree.
*Read our latest blog for an updated list of affected packages.
Conclusion
The September 8, 2025, NPM supply chain attack represents a watershed moment for JavaScript supply chain security. With 200+ confirmed compromised packages and billions of affected downloads, this incident demonstrates the cascading impact possible when maintainer accounts are compromised. The attack’s success through simple phishing—despite the technical sophistication of its targets—underscores that human factors remain the weakest link in software supply chains.
Organizations must treat this incident as a critical warning. The JavaScript ecosystem’s interconnected nature means that future attacks could have even more severe consequences. Immediate remediation is essential, but long-term security requires fundamental changes to how we manage, monitor, and secure our software dependencies.





