What is Risk-Based Vulnerability Management (RBVM)?
Learn about Risk-Based Vulnerability Management (RBVM) and its role in addressing security risks in today’s digital landscape.
Table of Contents
As modern enterprises expand their digital presence, they face an ever-growing volume of assets, ranging from cloud infrastructure to on-premises and off-premises systems (hardware and software), each introducing the potential for new vulnerabilities. Traditional vulnerability management methods struggle to keep pace with this rapid growth, often overwhelmed by the sheer number of vulnerabilities and unable to prioritize those that pose the greatest risk to the business.
This is where Risk-Based Vulnerability Management (RBVM) comes into play. Risk-Based Vulnerability Management is an approach that assesses, correlates, prioritizes, and remediates vulnerabilities based on the actual risk they pose to an organization. This results in more efficient use of resources and a stronger security posture, helping organizations manage vulnerabilities in a way that aligns with their business priorities.
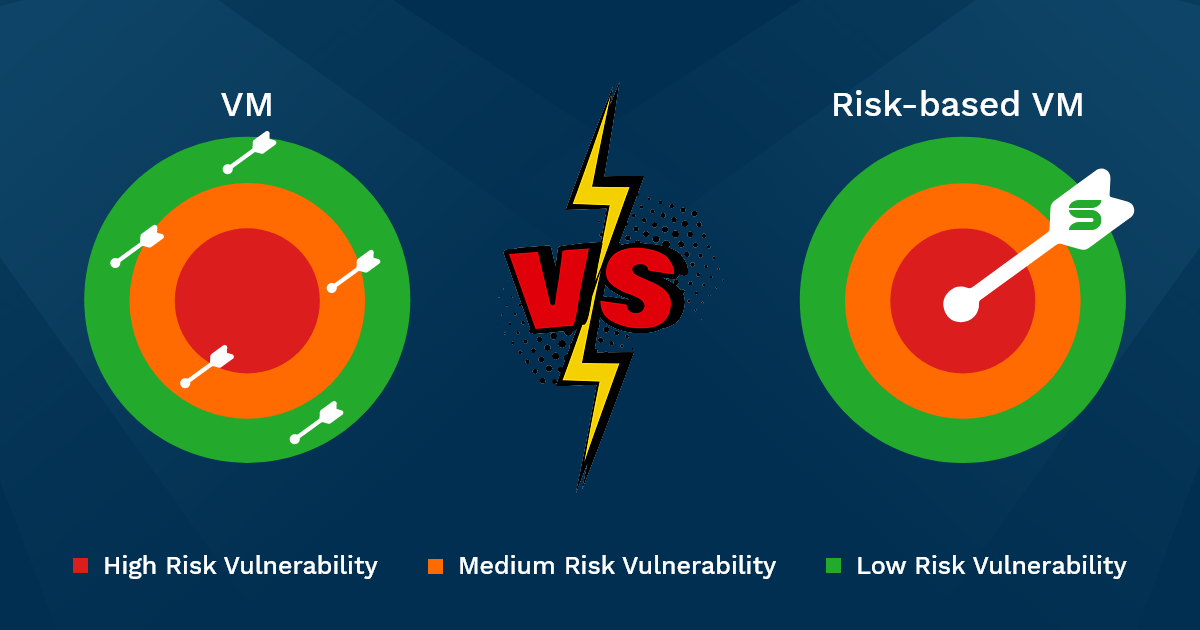
Risk-Based Vulnerability Management vs Traditional Vulnerability Management
Traditional Vulnerability Management primarily relies on scoring systems like CVSS (Common Vulnerability Scoring System) and CVE (Common Vulnerabilities and Exposures) to identify and assess vulnerabilities. In this model, vulnerabilities are usually ranked manually based on their severity scores, such as critical, high, medium, or low. While these scores provide a baseline understanding of vulnerability risks, they often fail to account for the specific context of an enterprise’s environment. Traditional methods treat all vulnerabilities within a certain severity range equally, regardless of how relevant or exploitable they are for the business, leading to inefficiencies and wasted resources.
For example, a vulnerability with a high CVSS score might be critical in one enterprise but irrelevant in another, depending on the impacted asset’s role, exposure, and the threat landscape. This approach can result in security teams spending time on issues that may have little to no impact, while more significant risks go unaddressed.
Risk-Based Vulnerability Management (RBVM) shifts this model by incorporating contextual data, such as asset criticality, exploitability, advanced threat intelligence, and business impact into vulnerability prioritization. Instead of relying solely on static scores, RBVM evaluates the risk a vulnerability poses in the specific context of the enterprise’s operations.
In this approach, a vulnerability that ranks lower on a CVSS/CVE scale may be more urgent to address if it exists on a critical asset or if there’s an active exploit in the wild. By taking these factors into account, RBVM ensures that security efforts are aligned with the organization’s risk landscape, enabling faster remediation of high-impact vulnerability.
| Features | Traditional Vulnerability Management | Risk-based Vulnerability Management |
|---|---|---|
| Focus | Identifying and patching vulnerabilities based on CVSS and CVE scores. | Prioritizing vulnerabilities based on their potential impact on the organization. |
| Factors considered | Technical characteristics of vulnerabilities (CVSS, CVE). | Technical characteristics, asset criticality, threat landscape, and business context. |
| Efficiency | May waste resources on low-impact vulnerabilities and remediation of high-impact issues might get delayed. | More efficient allocation of resources and faster remediation of high-impact issues. |
Benefits of Risk-Based Vulnerability Management (RBVM)
RBVM solutions enable enterprises to streamline their security processes, make better use of resources, improve their overall security posture, and many other benefits. Below are seven of the key benefits an RBVM solution brings to modern organizations.
- As enterprises grow, so does their attack surface, making it harder to track and secure every asset. An RBVM solution provides full visibility into vulnerabilities across all environments, correlating data from security tools and vulnerability scanners to ensure all assets are accounted for and prioritized, reducing entry points for attackers.
- RBVM focuses on addressing the most critical vulnerabilities by considering factors like asset context, severity, advanced threat intelligence, and business impact. This helps security teams allocate resources efficiently and reduce vulnerability backlogs by 80%.
- By unifying vulnerability risk management across infrastructure, cloud, containers, and/or applications, RBVM solutions seamlessly integrate into DevOps workflows, automating security checks and vulnerability assessments without slowing down the pipeline. This enables enterprises to deliver new software faster while maintaining strong security governance.
- RBVM provides a centralized view of vulnerability management across hybrid environments, whether on-premises or in the cloud, ensuring security consistency no matter the infrastructure’s size or diversity.
- As enterprises adopt new technologies like AI and IoT, a vendor-agnostic RBVM ensures security strategies stay effective by integrating seamlessly with any underlying infrastructure and tech stacks. It provides continuous updates to integrate seamlessly with new security tools and solutions.
- RBVM automates vulnerability tracking, prioritization, and remediation workflows, enabling faster resolution of critical vulnerabilities and reducing exposure time while easing the workload for security and development teams.
- By integrating into existing workflows, RBVM bridges the gap between security and IT/development teams, providing a unified platform for tracking, assigning, and remediating vulnerabilities efficiently.
By focusing on critical risks, automating workflows, and providing comprehensive visibility, RBVM helps enterprises strengthen their overall security posture and reduce the likelihood of attacks.
Key Components of RBVM
RBVM solutions leverage several key components that work together to provide a comprehensive approach to vulnerability management.
1. Asset Discovery and Inventory
An important aspect of RBVM is comprehensive and accurate asset inventory. This involves ingesting, continuously identifying, and cataloging all assets—whether they are on-premises, in the cloud, or part of containerized environments. RBVM ensures that no asset is left unaccounted for, providing a complete, up-to-date inventory that is essential for effective vulnerability management.
2. Vulnerability Correlation
Most teams don’t struggle with coverage but with visibility. Multiple vulnerability scanners across code, cloud, infrastructure, and containers generate thousands of findings daily, but these tools often don’t communicate with each other, leaving teams overwhelmed with large volumes of findings.
RBVM solution seamlessly integrates with multiple security tools and vulnerability scanners to ingest and unify vulnerabilities across the entire IT ecosystem. This includes infrastructure, cloud environments, containers, and/or applications. By correlating findings from various sources, RBVM creates a unified view of vulnerabilities, ensuring that no critical threats are overlooked.
3. Risk-Based Prioritization
The core component of RBVM is its ability to prioritize vulnerabilities based on risk, not just severity. It does this by taking into account factors such as asset criticality, exploitability, threat intelligence, and potential business impact. This ensures that the most dangerous vulnerabilities are addressed first, helping security teams focus on issues that matter the most to the business.
4. Contextual Risk Scoring
RBVM assigns a risk score to each vulnerability based on the severity from the source tool, CVSS score, threat intel, exploit information, tool weighting (user-managed variable), business context, and actual impact. This dynamic customizable scoring provides deeper insights into the true risk of a vulnerability, enabling security teams to make informed, context-driven decisions about remediation priorities.
5. Automated Remediation Workflows
To accelerate remediation time and reduce the burden on security and IT teams, RBVM solutions include automated workflows that streamline vulnerability remediation, from correlating and triaging vulnerabilities to ticket creation and escalation. The bi-directional integration with ticketing and messaging systems helps IT and development teams to work in their environment without switching platforms. This reduces manual effort, increases efficiency, and helps your vulnerability management team work at the scale of your enterprise.
6. Threat Intelligence Integration
Risk-Based Vulnerability Management (RBVM) solution provides real-time advanced threat intelligence feeds. It incorporates predictive measures such as EPSS, dark web monitoring, social trend analysis, and threat actor intelligence. This allows organizations to stay updated on emerging threats, active exploits, and changes in the attack landscape. By constantly correlating vulnerabilities with active threats, RBVM helps enterprises adjust their remediation priorities dynamically.
7. Reporting and Analytics
Comprehensive reporting and analytics are essential for monitoring progress and showcasing the effectiveness of a vulnerability risk management program. RBVM solutions offer customizable dashboards and detailed reports that provide visibility into vulnerability status, risk trends and summaries, SLA compliance, remediation progress, and more. These insights enable security leaders to make informed, data-driven decisions, communicate risks to stakeholders clearly, and help developers track their remediation efforts while offering leadership a clear view of overall performance.
8. Scalability and Flexibility
RBVM solutions are designed to scale with the organization as it grows. Whether dealing with thousands of on-premises assets or sprawling cloud infrastructure, RBVM solutions provide the flexibility to manage vulnerabilities across diverse environments without being tied to any specific vendor. This ensures that enterprises can continue to protect their expanding digital footprint without compromising security.
These key components ensure that RBVM solutions provide a holistic, risk-centered approach to vulnerability management, helping enterprises maintain a robust security posture in the face of evolving threats.
How Risk-Based Vulnerability Management (RBVM) Solution Works
A Risk-Based Vulnerability Management (RBVM) solution streamlines vulnerability management, ensuring that no critical vulnerabilities are overlooked and potentially lead to a breach. Below is a step-by-step overview of how RBVM works to empower the vulnerability management team or security professionals.
1. The first step in RBVM is to pull in data from existing asset inventories while also discovering any missing assets (from findings) to create the most comprehensive and accurate asset inventory.
2. After creating a complete and up-to-date asset inventory, the next step is to gain a unified view of all vulnerabilities discovered from infrastructure, cloud, container, and/or application security scanners that need to be managed.
3. The next step is assigning a risk score to vulnerabilities correlated in the above step, indicating how likely it is to be exploited and what damage it could cause if left unaddressed.
4. After getting the risk score, vulnerabilities are prioritized based on their potential risk to critical assets, enabling teams to focus on high-impact issues first.
5. The RBVM solution automatically escalates issues and assigns them to the appropriate teams or owners, streamlining the remediation process without the need for manual intervention.
6. It continuously monitors for new vulnerabilities and adjusts risk scores in real-time as the threat landscape evolves.
7. RBVM provides detailed reports and analytics, helping teams track progress, measure risk reduction, and communicate results effectively.
Measure, Manage, and Mature Vulnerability Management Program
A successful vulnerability management program begins with a clear understanding of your current security posture, which requires continuous measurement and tracking. By regularly assessing the number and severity of vulnerabilities, the time to remediation, and overall risk reduction, organizations can benchmark their performance and identify areas for improvement.
Leveraging comprehensive reporting and analytics from a Risk-Based Vulnerability Management (RBVM) solution allows security teams to make data-driven decisions, track key performance indicators (KPIs), and demonstrate measurable progress over time. The ideal RBVM solution provides insights into team performance, helping identify areas where additional resources or training may be needed. It also highlights which tools teams are adopting more effectively, enabling better decision-making around resource allocation and team development.
The focus on metrics helps ensure that vulnerabilities are being addressed effectively and that the program is aligned with organizational goals.
Managing vulnerabilities goes beyond detection and remediation; it involves refining processes, enhancing collaboration between security and IT teams, and automating workflows to optimize efficiency. As the vulnerability management program matures, enterprises should continuously adapt to evolving threat landscapes and new technologies.
Implementing an RBVM solution allows for scalability, better prioritization, and seamless integration with other security tools and vulnerability scanners, ensuring that the program can evolve in line with the organization’s growth.
By measuring progress, managing risks proactively, and maturing the program as needed, enterprises can strengthen their security posture and build a resilient defense against vulnerabilities.
Unified Vulnerability Management (UVM)
Unified Vulnerability Management (UVM) expands on the principles of Risk-Based Vulnerability Management (RBVM) by offering a holistic view of vulnerabilities across all environments, from applications and cloud to infrastructure and containers.
Organizations manage a diverse array of assets that can introduce vulnerabilities from multiple sources. UVM addresses this complexity by focusing on unifying these vulnerabilities into a single platform, allowing organizations to identify, prioritize, and respond to threats based on a comprehensive understanding of their entire attack surface.
Unlike traditional vulnerability management which may treat vulnerabilities in separate silos, UVM provides centralized visibility, helping security teams correlate and prioritize vulnerabilities across all areas of the organization. This integrated approach not only allows for better context and prioritization but also streamlines remediation processes by ensuring that all vulnerabilities are managed consistently across different systems and teams.
A comprehensive vulnerability management strategy combines RBVM principles with the advantages of UVM, which is why these terms are now often used interchangeably. Based on the scope of your vulnerability management program, you can centralize just infrastructure vulnerabilities or include all vulnerabilities, including applications in a single platform.
Managing Vulnerabilities and Addressing Risks with the ArmorCode Platform
ArmorCode provides an AI-powered platform for vulnerability management teams to address risk comprehensively. It allows for the unification, prioritization, and remediation of vulnerabilities across infrastructure and cloud environments, as well as the entire technology landscape, including applications, containers, and distributed assets.
With ArmorCode, even if separate teams manage vulnerabilities for infrastructure and applications, leadership can easily monitor key performance indicators, track progress, and communicate specific areas of concern effectively.
The ArmorCode Platform simplifies the complexity of vulnerability management, helping organizations reduce their risk footprint, optimize resource allocation, and achieve a stronger, more resilient security posture.
3 Mandatory Steps to Mature your AppSec Program Today
Read this whitepaper to discover how to mature beyond scanning and burn down your critical security debt by >80%.


