Blog
Insights from experts on Exposure Management, AI security & more

Blog
Burn Down >80% of your Critical Security Tech Debt with a Mature AppSec Program

Blog
Bridging the Gap: How ASPM Ensures Seamless Collaboration Between Security & Development Teams

Blog
AWS S3 Bucket Security: The Top CSPM Practices

Blog
Managing Risk with Secure Product Lifecycle Management

Blog
Why ASPM is a Must-Have for Modern Application Development

Blog
Cybersecurity Landscape: Unpacking 2023 and Anticipating 2024

Blog
The Cyber Insider: Week 1/29 – 2/4
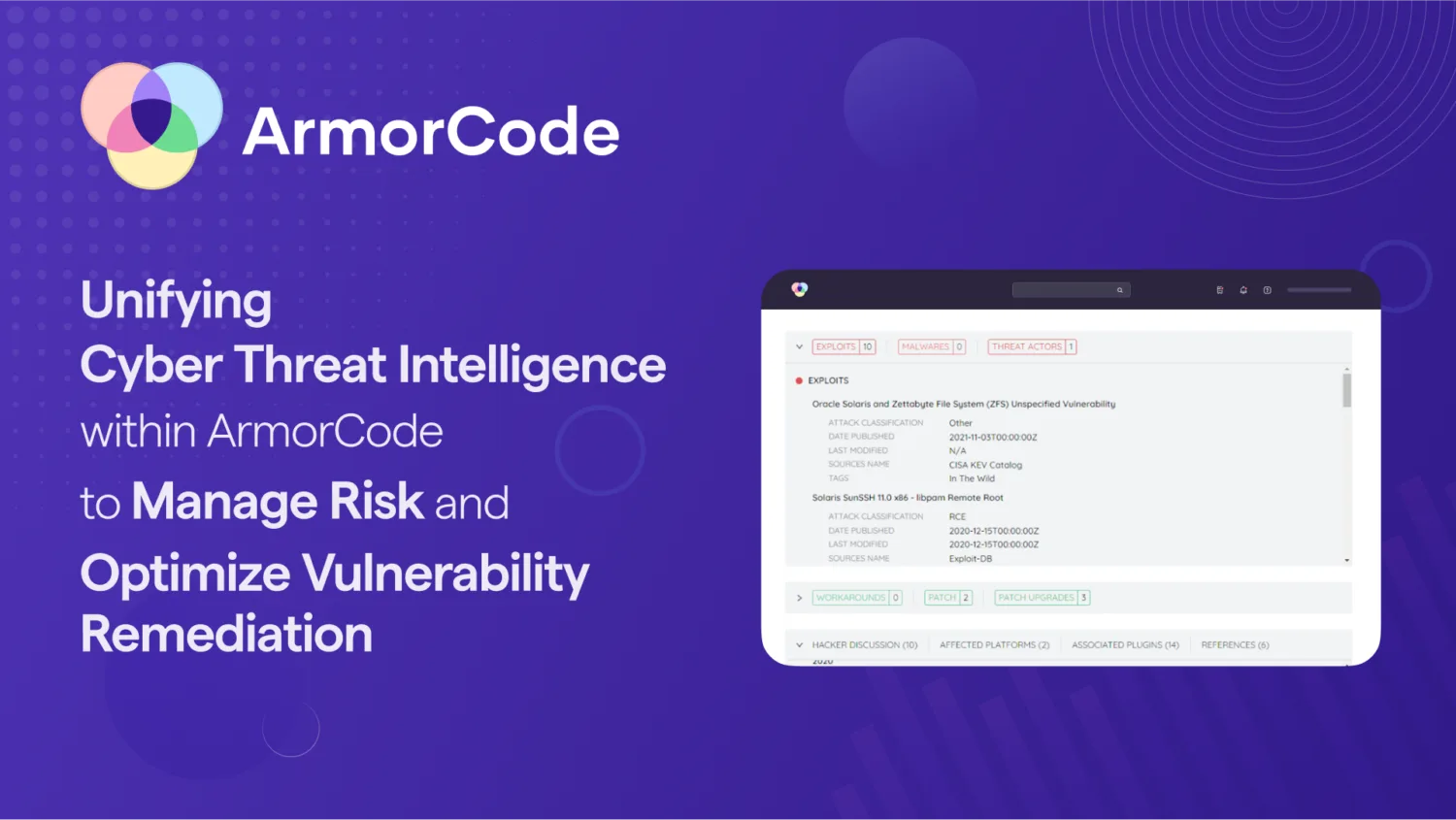
Blog
Unifying Cyber Threat Intelligence to Prioritize Vulnerability Remediation & Manage Risk

Blog
ASPM vs CSPM: What’s the Difference?

Blog
Why take a Risk-Based Approach to Vulnerability Management?

Blog
The Cyber Insider: Week 1/22 – 1/28

Blog
